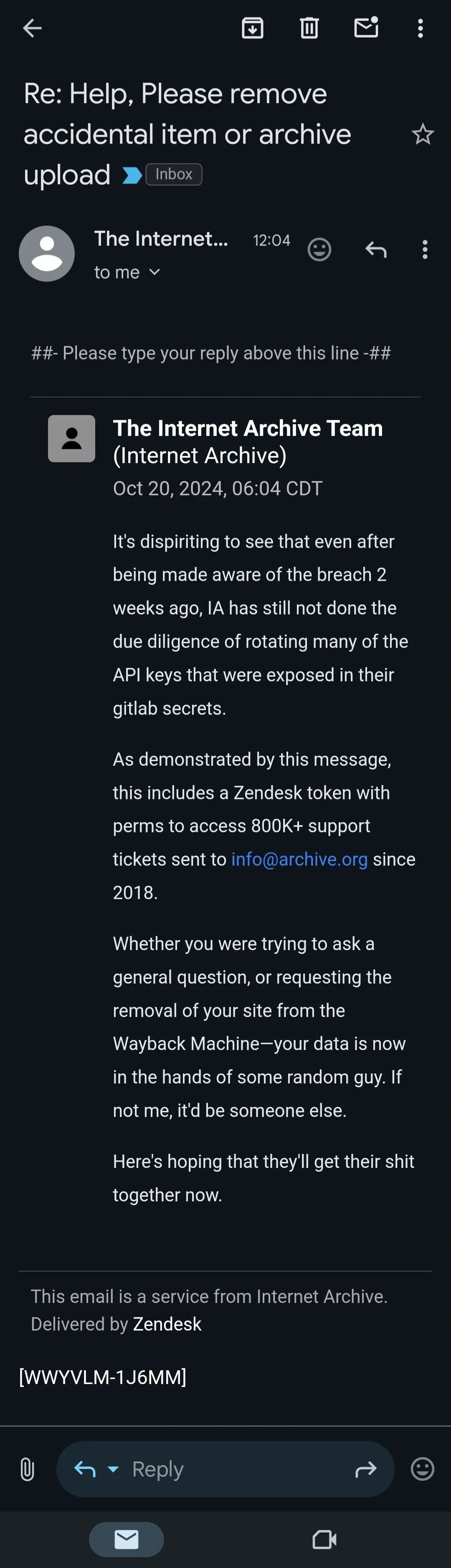
Hackers acting as if they're doing a public service by bringing down a free publicly accessible tool is a new level of assbackwardness.
If the goal really was to force IA to increase their security, they would've tried to consult with them. This is more about notoriety and chaos and the hackers have no moral ground to stand on.