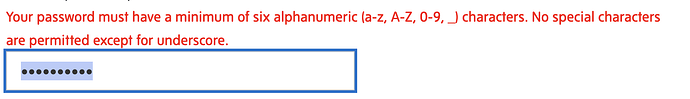
"Your selected password is already being used by SwiftyFan05. Please choose another password."
Mildly Infuriating
Home to all things "Mildly Infuriating" Not infuriating, not enraging. Mildly Infuriating. All posts should reflect that.
I want my day mildly ruined, not completely ruined. Please remember to refrain from reposting old content. If you post a post from reddit it is good practice to include a link and credit the OP. I'm not about stealing content!
It's just good to get something in this website for casual viewing whilst refreshing original content is added overtime.
Rules:
1. Be Respectful
Refrain from using harmful language pertaining to a protected characteristic: e.g. race, gender, sexuality, disability or religion.
Refrain from being argumentative when responding or commenting to posts/replies. Personal attacks are not welcome here.
...
2. No Illegal Content
Content that violates the law. Any post/comment found to be in breach of common law will be removed and given to the authorities if required.
That means: -No promoting violence/threats against any individuals
-No CSA content or Revenge Porn
-No sharing private/personal information (Doxxing)
...
3. No Spam
Posting the same post, no matter the intent is against the rules.
-If you have posted content, please refrain from re-posting said content within this community.
-Do not spam posts with intent to harass, annoy, bully, advertise, scam or harm this community.
-No posting Scams/Advertisements/Phishing Links/IP Grabbers
-No Bots, Bots will be banned from the community.
...
4. No Porn/Explicit
Content
-Do not post explicit content. Lemmy.World is not the instance for NSFW content.
-Do not post Gore or Shock Content.
...
5. No Enciting Harassment,
Brigading, Doxxing or Witch Hunts
-Do not Brigade other Communities
-No calls to action against other communities/users within Lemmy or outside of Lemmy.
-No Witch Hunts against users/communities.
-No content that harasses members within or outside of the community.
...
6. NSFW should be behind NSFW tags.
-Content that is NSFW should be behind NSFW tags.
-Content that might be distressing should be kept behind NSFW tags.
...
7. Content should match the theme of this community.
-Content should be Mildly infuriating.
-At this time we permit content that is infuriating until an infuriating community is made available.
...
8. Reposting of Reddit content is permitted, try to credit the OC.
-Please consider crediting the OC when reposting content. A name of the user or a link to the original post is sufficient.
...
...
Also check out:
Partnered Communities:
Reach out to LillianVS for inclusion on the sidebar.
All communities included on the sidebar are to be made in compliance with the instance rules.
Somebody isn't sanitizing their inputs properly. Like putting a bandaid on a heart attack
Whenever I see something like this I just laugh because you're exactly right. Something isn't being handled properly and their dev team just proved they don't know how to do some basic handling. Every API library in JS and restful API I know of handle special characters. If they wanted they could base64 encode it over the wire. Then you're exactly right, if the database "can't handle it" more than likely it's a home spun database connection where they're serializing it themselves (which even then this is solvable), but even then that proves that they make poor choices.
if the database "can't handle it" [...] that proves that they make poor choices.
Exactly, the database should never even have to handle the password in it's original form and hashing algorithms don't care about special characters.
This is like when I was in my twenties working at a crappy grocery store with a MoneyGram inside of it. I live in Washington state, and at the time, if your last name was less than five characters, you would have asterisk's in your license number. The MoneyGram system wanted people's license numbers but was unable to recognize a license with an asterisk. It happened pretty rarely, but it always happened to people whose last names were four characters or less long. Five letters in your last name and you were gold. To make the transactions happen, I would just do the whole license number minus the asterisk.
Anyway, Washington changed how it generates license numbers so its a moot point anyway but I don't think MoneyGram ever spent a dime to fix this since it only affected a small number of people in one US state.
Sometimes I wonder if I'm even fit for employment as a developer and then I see shit like this where I wonder who and what happened for this to even become an option?
Always remember there is someone much cheaper than you who will do a much worse job, but be more arrogant about it
Seems to be they're dropping the passwords in the database in plain text, but they're deathly afraid that someone will drop a '; in there or something and the insert will break.
Notwithstanding that storing passwords in plain text is a slapping with the 10 foot rubber chicken, but mysqli_real_escape_string() or any number of other similar solutions are indeed a thing that exists. A prepared statement would work, too.
but mysqli_real_escape_string() or any number of other similar solutions are indeed a thing that exists. A prepared statement would work, too.
You make it sound as if a prepared statement is a last resort. I would turn that around: as a rule always use prepared statements when dealing with user input. It's very easy to forget a single call to mysqli_real_escape_string().
Which is ridiculous because it's going to hash down to the same character set. There's no way they're storing your password with special characters unhashed, right?
Lol I recently have found the opposite!
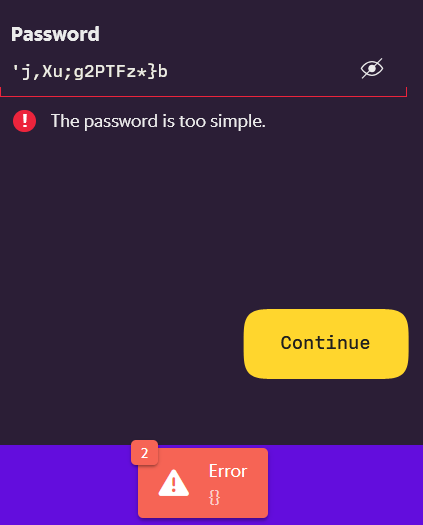
Might be a minimum of 16 chars. Or the parsing is broken and treats the ' as the end of the password
Yeah, I'd consider anything less than 20 characters broken. Much too likely that it's contained in a rainbow table, regardless how many special characters you use. Can I remember many 20 character passwords? No, but my password manager can.
That's a big rainbow table. Like, with just precomputed values and random ascii character passwords it's on the order of 10^42^ entries. You can shave that down a bit probably with all the tricks rainbow tables use, but I think you're safe.
I let my password manager create 32 char passwords, that should be enough for a while. But of course then you have websites that throw you a 'your password is too long' message and have you find out by trial and error that they only accept 12 characters.
Or the off-by-one errors where they insist that 24 chars are the max, but in reality they accept 23. Probably never tested the limit.
Or websites that truncate your password after X characters when registering, but not when logging in, so you end up with an incorrect password and good luck finding out which limit the registration page actually uses.
Fandom is gross anyway. Contributing to independent wikis is a much better use of your time. https://getindie.wiki/
It's not Fandom
they don't specify a limit so 64 character password it is.
Go all in, 1024 character password.
They'll accept it, but won't tell you they ignored everything after character n, and their login page won't take anything but the "correct" password so you'll be spending some time figuring out the actual character count limit...
No, they'll accept it. Then on the log in page tell you the max limit is X, even though on the password creation page, the password length you used was X+Y
I have experienced this far too many times.
Even worse the password was accepted in full when registered, but the login field won't accept the full length.
My previous bank forced 8 characters with only numbers and letters.
Hunter2
I don't get it, why did you type all asterisks‽
What's not to get? He made his password 7 asterisks. Funny, because it's the same as mine.
Some months back, there was a thread here on Lemmy where people were discussing western names written using Chinese characters. Phonetically, the names will sound alike. But meaning-wise, the characters will result in a Correct Horse Battery Staple-esque string of words.
Which is why I have since decided to make passwords by typing random names into a Chinese name generator and using the English translated result.
Sounds like a lot of work, but the way I see it, trying to think of new passwords is always work so I might as well have fun with it.
64 characters picked at random in [a-zA-Z0-9_] is perfectly fine if password is your only option. Special character do not increase significantly the difficulty of bruteforcing it, but introduce the risk of having to manually type "}à.å÷Â!!ç-×ô@¸Á¢±ãÕß>>úÓ}¼º¤«<_`àÅû§Æ]*ÂñçÌÿ§à®&ܱ=Ú-´ð¹é$.>=;Ö if something goes catastrophically wrong.
Not being allowed to use special characters can be a sign of the website saving your password in plain text.
It's actually nice they have underscore. 😀
Yes because if you choose 8 characters at random, with 25 small + 25 big letters and 10 numeric, it* only 60^8
= 167,961,600,000,000 combinations.
I think the problem is more if the system allows brute force with thousands of erroneous attempts.
Then statistically any hacker can attempt several accounts, and ultimately get lucky. But by all means, put the responsibility to the user, users are the experts right!?
I never got the frantic excessive entropy mindset, when the problem is much simpler to not allow crackers endless attempts. You can allow 50 attempts, and chances would be very slim to guess even pretty moronic passwords.
What's even worse is when they REQUIRE big and small and numbers to maximize entropy, they actually make statistically FEWER attempts necessary to brute force it.
A standard Microsoft introduced in the 90's, and FUCKING almost everybody is using, despite it's a 100% moronic requirement.
Instead just warn against passwords that can be guessed by logic, or can be found in a dictionary.
Most websites don't allow multiple failed logins and, even if they did, the network latency alone would make brute force attacks useless. The point of having a high entropy password is to protect against hackers brute forcing a leaked database of hashes. Having different passwords for every website also protects against this so, as usual, the answer is "just use a password manager".
The point of having a high entropy password is to protect against hackers brute forcing a leaked database of hashes.
I don't think you need to worry about that in this case, the special character restriction suggests to me that they don't hash it.
Try this one, has lots of special characters: a_a_a_a_a_a_a_a
recently did one that only cared about being very long, so i typed thispasswordisfuckinglong and it took it
"for best results, your password should be the street you grew up on or your favourite book"
I mean, 63^6 is a lot of possibilities, but just make the password longer to increase its security.
Blocking out special characters is dumb, but as others have pointed out, they're probably not sanitizing inputs.
Use a password manager
I hate these arbitrary limitations of 16 characters, 25 is unbreakable and some sites won't allow longer than 16 20, I've even had one site not allow over 6.
At least if you ever forget it, they'll be able to email it to you.
Ah, I've done that before, 1/100 odds it's because someone doesn't want to fuck with RegEx.