this post was submitted on 22 Jan 2024
666 points (94.6% liked)
People Twitter
7400 readers
1685 users here now
People tweeting stuff. We allow tweets from anyone.
RULES:
- Mark NSFW content.
- No doxxing people.
- Must be a pic of the tweet or similar. No direct links to the tweet.
- No bullying or international politcs
- Be excellent to each other.
- Provide an archived link to the tweet (or similar) being shown if it's a major figure or a politician.
founded 2 years ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
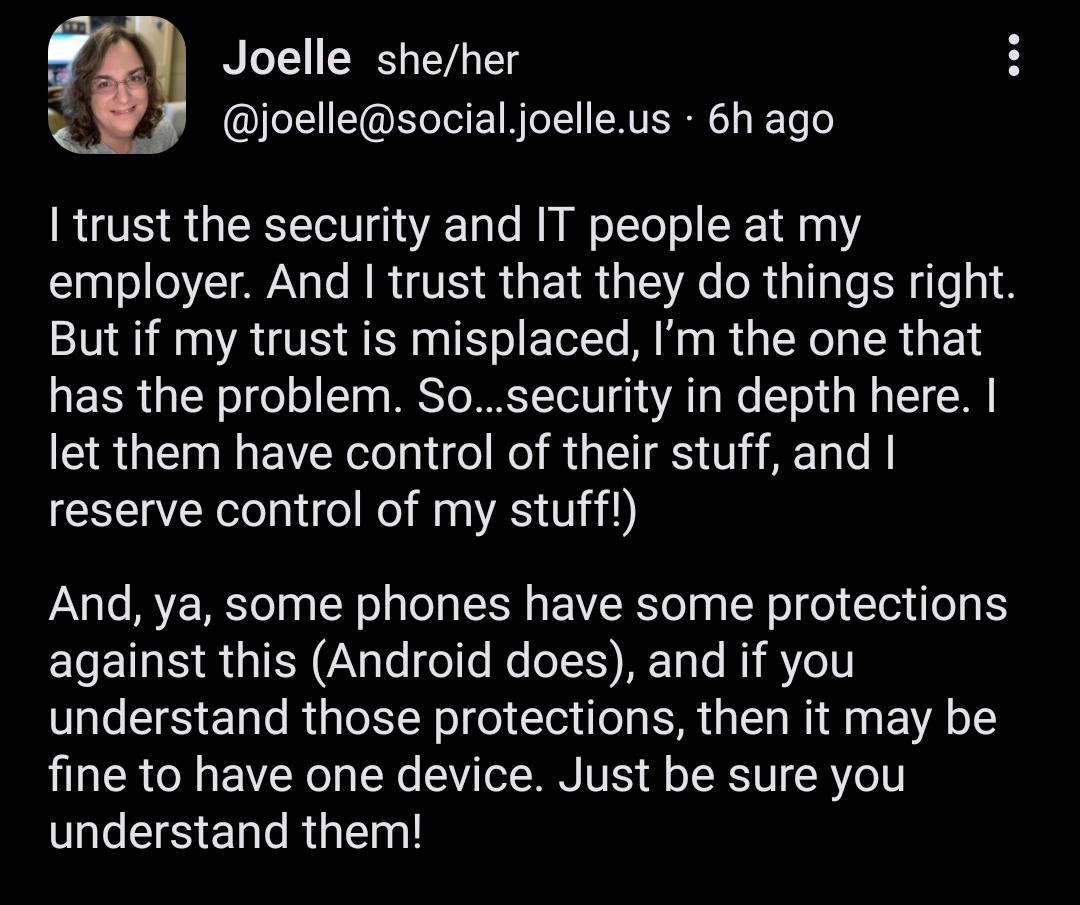

Can you elaborate? I have simple mdm on my work phone and would like to know exactly what they see and can do
Not that I am hiding anything. It’s more curiosity at this point
Posted from my personal phone
This depends on the configuration of the MDM and the MDM vendor. For example, most MDM deployments to Android for instance conform to Android For Work, which functions in practice to a virtual machine from a user's perspective, and doesn't have access to a non workspace content. iOS has a similar functionality which, while less commonly used, is there specifically for use on personal devices to sandbox off 'work' content where pervasive features like factory resets and access to phone logs and sms records don't function, and you can't access the more advanced features without having purchased the device via a corporate account.
SimpleMDM has a credit card-less trial which you could set up to see what features exist and how they work from the vendor side. You won't have access to some of the 'supervised' features without being a business,but you can see the buttons offered when you aren't a corporate-purchased device readily enough.
For corporate owned devices, the rules are very different though.
I have a little experience with Microsoft’s intune and there are different ways to register devices. Someone feel free to correct me because I don’t feel like logging in to double check. Company owned devices have more control and can restrict apps, lock, full wipe, etc. Personal or “bring your own” devices are much less restricted. I can’t lock, wipe, or restrict apps. For the personal devices, it’s more about giving secure access to the companies resources and not really controlling the device. I work for a small business and only use this to setup access to non important documents for employees in the field so I know just enough to be dangerous.
I can’t read your emails, text messages, I can’t remote into your phone without your permission. The info we have is very limited. You know how we can see that information? If you gave us your phone and password :-)
So if the info it provides is very limited, why are companies pushing for it? Why should I install it on my personal phone so I can access Teams and Outlook?
Because if you are accessing company data, the company needs to ensure it’s safe. If you don’t want outlook or Teams access, you don’t have to enroll your device. In some cases companies will purchase a corporate owned device for you. An MDM allows companies to restrict copying data from work to personal and vice versa. If your device gets stolen and is compromised, it allows the company to wipe it. It can also locate the decide if it’s lost.
So is having MDM useless if you also have corporate webmail? Because not having MDM on my phone means I just go to my webmail site on my phone for email, and I can copy there if I need to.
Google's "Find Device" allows for finding and wiping a device by default on Android.
So it's really just those two features? Doesn't really seem worth the hassle unless there's something else they're getting out of it.
The data is valuable and it provides some amount of data security. Any MDM worth a shit will wall off your Android with a work profile and that’s the only part that’s actually controlled by the MDM. They can also mandate a minimum level of security before accessing the work profile.
Webmail can be used as a workaround, but allowing it is more of a convenience issue than a security consideration. Depending on your security team it could be a major hole or not an issue. Authentication requirements can offset the vulnerabilities somewhat, such as short timeouts, MFA, etc.
In my experience, users like you are what make MDM a requirement in any environment. People that refuse to participate in any security processes because they think they know better than the people whose job is literally cybersecurity are almost always the cause of major incidents. That’s how my current employer got a huge ransomware attack and why I’m not allowed to install anything on my phone or laptop without spending several hours on hold with the help desk.
Gotta love getting down voted for trying to learn more about a topic. Looks like Reddit culture is seeping in here.
Anyway, when you say:
What does that mean? I thought MDM was just making it so I couldn't copy data and that my employer could wipe/locate my phone. But it sounds like you're saying it's actually doing something more like creating a separate environment, almost like a VM, on my phone? Or is it different than that? My work MDM said they want to look at applications that you have installed. That was too much of a privacy invasion for me, so I chose not to use work apps on my phone.
Yeah, our IT systems would be exponentially more secure if we didn't have users too. One can dream, I suppose.
That’s something that I never understood, is the claim that default OS is just not secure… well then put all your dev hours into fixing that…