I need to ask a small favor from the good people of Lemmy.ml Community.
In short, I accidentally wiped the metadata partition on my Poco F3 and now I can't boot into the OS and access my data. I have a lot of pictures, videos and other stuff that I would hate to lose, because of a mistake. But all that is still on the phone, I just can't boot the phone to access it.
Thankfully, there is a way to fix this by creating a full backup of the phone with adb, then using a HEX Editor to manually look through that gigantic file and try to find the files that were in that metadata partition.
A huge thanks to bluet33th, a user from XDA Forums, without whom I would be helpless and couldn't do any of this. It might be a bit complicated and manual process, but it is possible. He explained everything in great detail here, so check it out, especially if you are facing the same problem, this will help you tremendously: https://xdaforums.com/t/how-to-recover-data-if-metadata-partition-was-deleted.4686789/
In order to find these files and put them back where they belong, I need your help, because I have to know their names, exact sizes and at least part of their content, so that I can search for it. Because I'm searching for a specific text in a text file that is 128 GB in size.
I have already tried this on another Xiaomi phone, to make sure this procedure works on Xiaomi phones and it does, but that phone had HyperOS with Android 14 and since every phone and android version is probably different, in order to be sure, I need this information specifically for Poco F3 with Android 13.
It doesn't take long, but if you don't have the time to look inside your metadata partition and tell me which files are inside of that partition and their sizes in bytes, you can just make a backup of the metadata partition and sent it to me, and I'll do the rest of the work.
Here are the steps on how to create a backup:
- Turn on your phone and boot into
TWRP, then connect your phone to a PC, type cmd inside Windows search and run cmd, then position cmd into your platform-tools folder (if you flashed your ROM, you should already have the necessary drivers installed for the next steps to work). For example, if your platform-tools folder on Windows is inside C:\platform-tools, all you need to type into cmd is: cd C:\platform-tools
You can also just go inside your platform-tools folder and type cmd in the address bar and the cmd will start already positioned inside that folder.
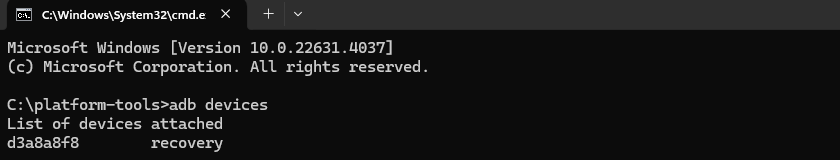
- Then type
adb devices and you should see your device, if you do, that means that all the drivers are successfully installed and your phone is detected.
- Type
adb pull /dev/block/by-name/metadata
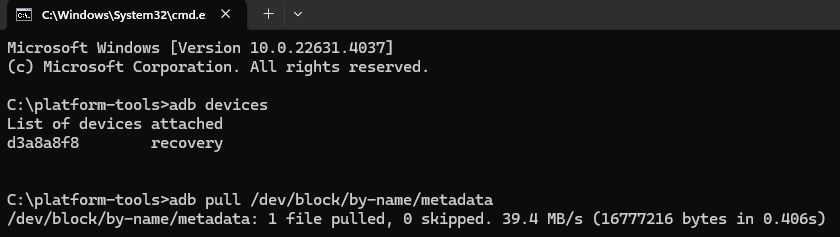
- After that, you should see a file named
metadata inside C:\platform-tools. That is the file that I'm looking for and as you can see, it takes just a few minutes to get it.
You can skip the next steps (5 and 6), but I'll explain them, just in case someone wants to extract these files for themselves, so that you have them in case something like this happens to you. Of course, you can also proceed to extract the files and tell me their names and sizes.
Here is what you need to do:
-
Extract the content of the metadata file, you can use a software like 7-Zip. Go inside that extracted folder, then into vold > metadata_encryption > key
-
Inside of that key folder, you should see a few files. These are the important files and save them somewhere safe in case you ever need them. Since I don't have them anymore, in order to recreate them, I need to know their exact names and sizes in bytes. You can check the size of every individual file by right clicking on the file and choosing Properties. Then look under Size, not Size on disk, and in parenthesis, you should see the size in bytes.
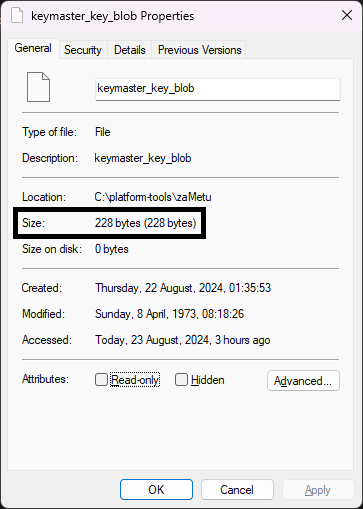
Please, if you could check the size of every file and write down which file has what size. I would really appreciate it.
I'm specifically looking for someone who has a Poco F3 with Android 13 and MIUI, because I'm not sure if HyperOS changed something, so maybe the number of files or their size is different. But feel free to post the information even if you have HyperOS, but please mention that, so that I am aware of it.
Thanks a lot for your help, it really means a great deal.













