Scolding0513
The truth of the matter is, until we make XMR easy to obtain/use for consumers and especially, easy to onboard for business owners, our message will fall short.
this means coming out with easy to use and understand software and even hardware. XMR ATM development should be much bigger than it is right now. Also, we should have an out of the box solution for business owners like a POS software or even a little hardware gadget.
By the way, is the monero network even prepared for such a thing in terms of speed? at what point during the transaction on-chain can the payment be considered safe to say that it's confirmed or that it can't be retracted somehow?
i think they delisted it for Germany recently. anyway get off of DumbassGPT lol
No. No no no no no no no NO. Do NOT federate with big tech. good lord people simply do not learn their lesson.
https://ploum.net/2023-06-23-how-to-kill-decentralised-networks.html
https://en.wikipedia.org/wiki/Embrace,_extend,_and_extinguish
was a type-in or from google search cant remember. google has big issues with phishing domains
fuck.. looks like i fell for phishing. or rather, my friend did, they were using my account. well, lesson learned i guess. ill delete this post
They withdrew all the XMR themselves after converting everything into XMR
Some more info:
At around 5:08-ish UTC Time (June 5), I tried to login, but couldn't because of this message:
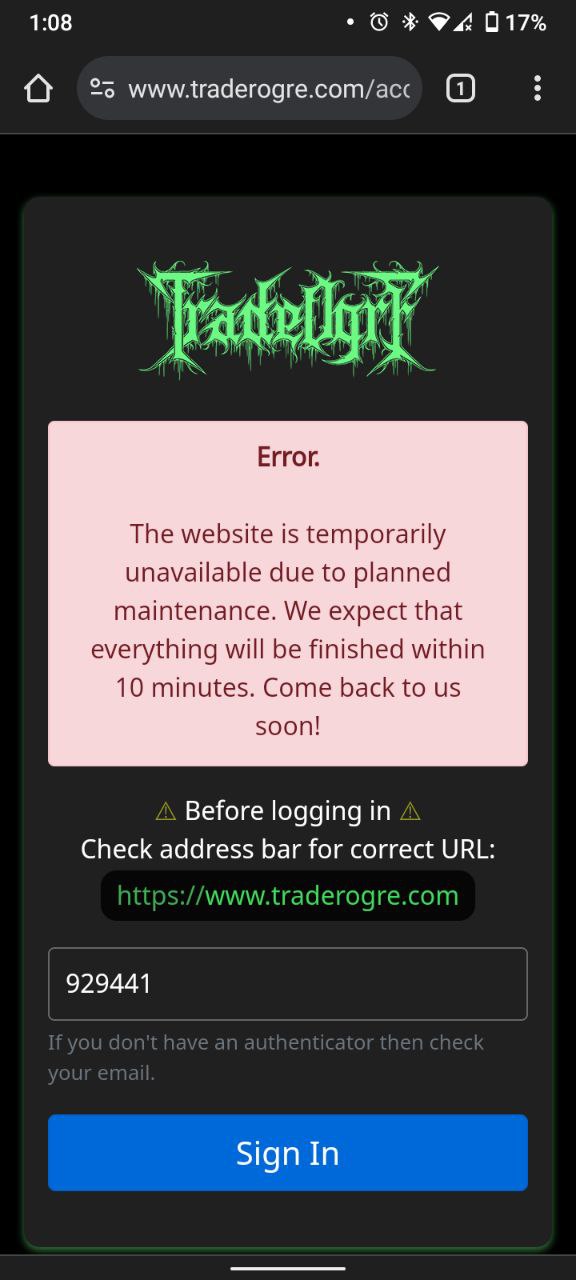
I had a little over 1XMR in my balance. My USDT was about 75 dollars. I had maybe 40$ in an order for XEQ i think. 30$ worth of satox. idk exactly. But you can see in the screenshots below that 1.6XMR was withdrawn out, which is approx what i had put in, comparing to my mental notes about what i was keeping track of, of how much xmr i sent in.
Here you can see all the XMR was withdrawn out of the account! At the exact time of the maintainence!
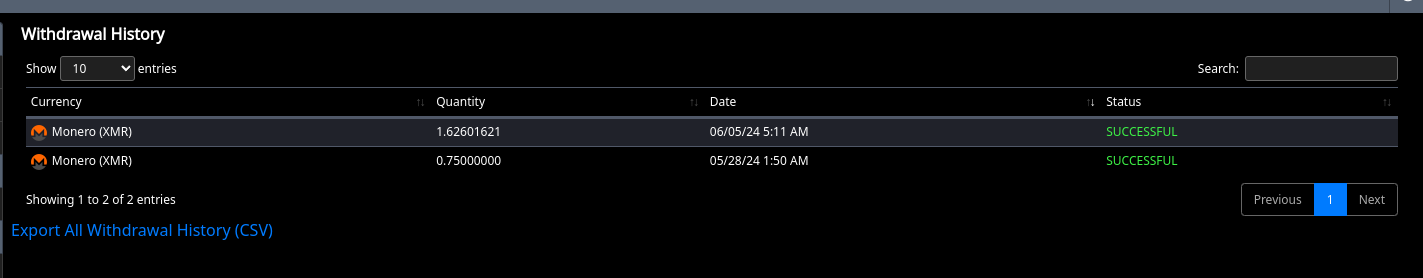
anyway When I was able to log in around 5:30UTC, I discovered everything had been liquidated. I don't mind showing you guys my full balance history
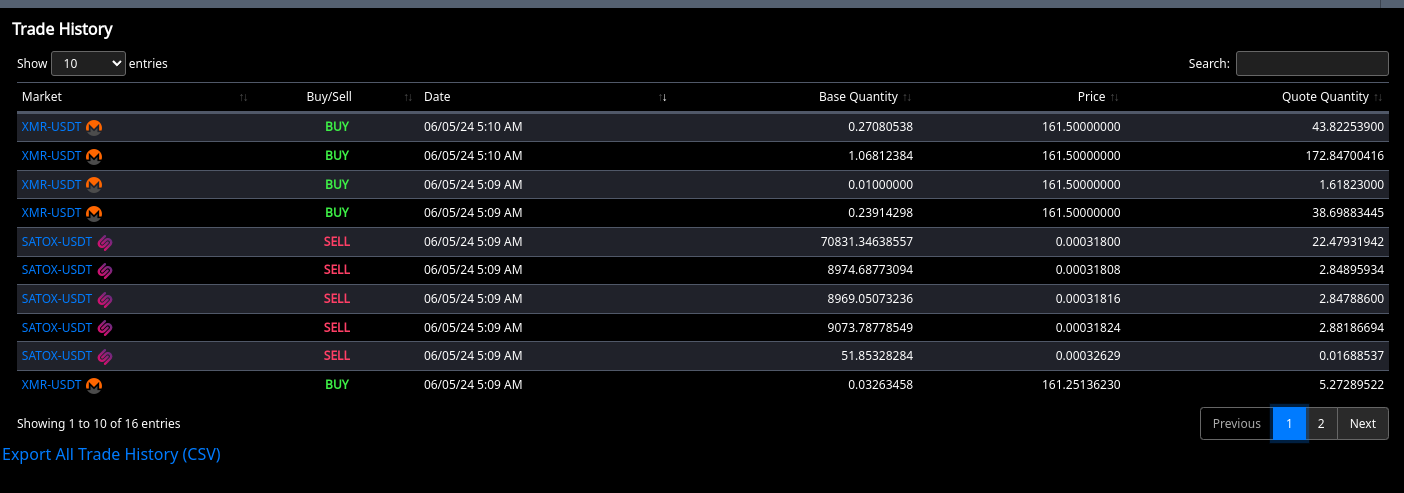
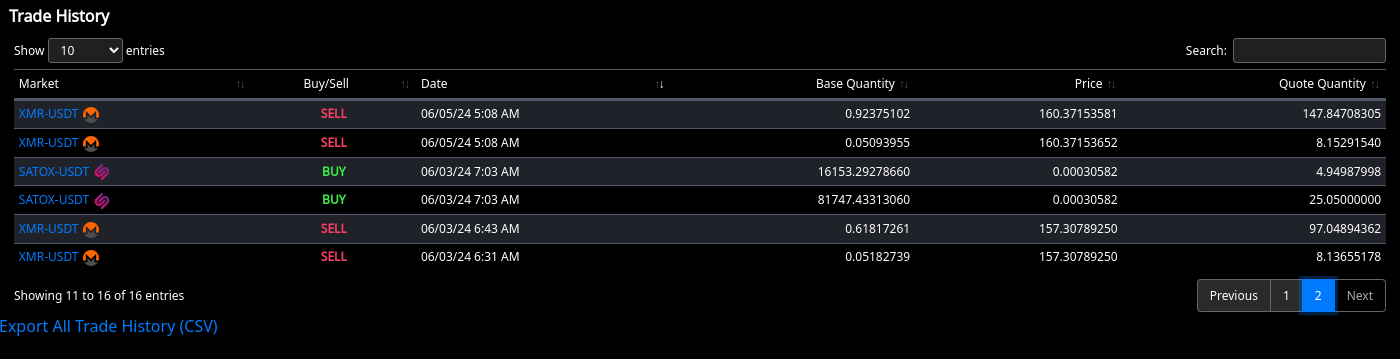
Their scam is very dirty. They do "maintenance" at a random time, for 10 minutes, because it's likely you wont log in during that time. Then they liquidate your shit and transfer it out and then they would probably say something like, "Oh your account got hacked into, nothing we can do".
But I just happened to try and log in exactly when they were doing it.
thanks for the additional info.
tor project needs to make a big announcement or something, because basically you can consider these nodes as being run by the fucking NSA/5eyes. this is really bad. one of the reasons i dont trust TOR alone for certain things anymore.
please dont say privacy focused then drop a google play link 😂
looks like 20% of guards are run on Hetzner gear. this is really bad considering they are knowm to be backdoored by feds. yet somehow everyone forgot, like they always do. sad shit.
interesting stuff, thanks for the info.
also did you see this in the paper?
In Timed Sync Response messages from a Tor client node to its outgoing hidden service peers, the last address in peer list is certainly different between different Timed Sync Response messages because only unshared onion addresses are sent. On the other hand, all Timed Sync Response messages from a Tor hidden service node to its outgoing hidden service peers have the same the last onion address in peer list, which is always its own onion address. Therefore, the repetition of the last address of Timed Sync Response messages from a Monero Tor hidden service node to its outgoing Monero Tor hidden service peers can be exploited by an attacker to identify incoming Monero Tor hidden service peers from incoming Monero Tor client peers and obtain its onion address.
is this a bug or a feature? have you spoken to anyone in the tor community about this? is there a going to be a mitigation for this? this seems concerning, yet I've seen no one talk about, which is even more concerning.
Edit: my bad, I forgot this is a Monero thing lol, not a TOR node thing