this post was submitted on 28 Sep 2023
324 points (75.7% liked)
Games
32671 readers
737 users here now

Welcome to the largest gaming community on Lemmy! Discussion for all kinds of games. Video games, tabletop games, card games etc.
Weekly Threads:
Rules:
-
Submissions have to be related to games
-
No bigotry or harassment, be civil
-
No excessive self-promotion
-
Stay on-topic; no memes, funny videos, giveaways, reposts, or low-effort posts
-
Mark Spoilers and NSFW
-
No linking to piracy
More information about the community rules can be found here.
founded 1 year ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
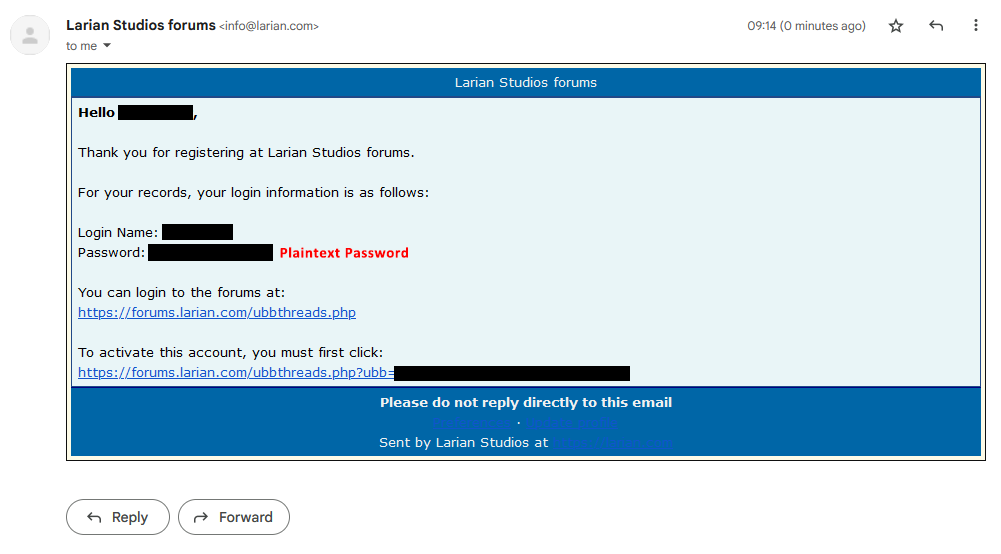
Yes, which is why they're vulnerable to mitm and local sniffer attacks.
Have you found a mitm attack on TLS?
This guy's a fucking clown, I'm sure he's like 15
Not without compromised certificates they haven't. You can tell because if they did they'd be world famous for having destroyed any and all internet security. Then again, they'd probably already be famous for having figured out a way to salt, hash and store passwords without ever holding them in memory first like they claim to do above, so maybe someone is lying on the internet about their vague "proprietary network protocols".
Oh yeah, this guy is a hoot.
I haven't looked into it but I was wondering about the logistics of setting up a federated honeypot for server side stream sniffing to build a plaintext email/password database.
Man, you sound like you're just using random words you heard in class. Clearly you have no clue how user registration actually works, let alone backend development.
Well it's a good thing your opinion has no effect on reality.