this post was submitted on 30 Jun 2024
2315 points (99.4% liked)
Malicious Compliance
21007 readers
1 users here now
People conforming to the letter, but not the spirit, of a request. For now, this includes text posts, images, videos and links. Please ensure that the “malicious compliance” aspect is apparent - if you’re making a text post, be sure to explain this part; if it’s an image/video/link, use the “Body” field to elaborate.
======
-
We ENCOURAGE posts about events that happened to you, or someone you know.
-
We ACCEPT (for now) reposts of good malicious compliance stories (from other platforms) which did not happen to you or someone you knew. Please use a [REPOST] tag in such situations.
-
We DO NOT ALLOW fiction, or posts that break site-wide rules.
======
Also check out the following communities:
[email protected] [email protected]
founded 2 years ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
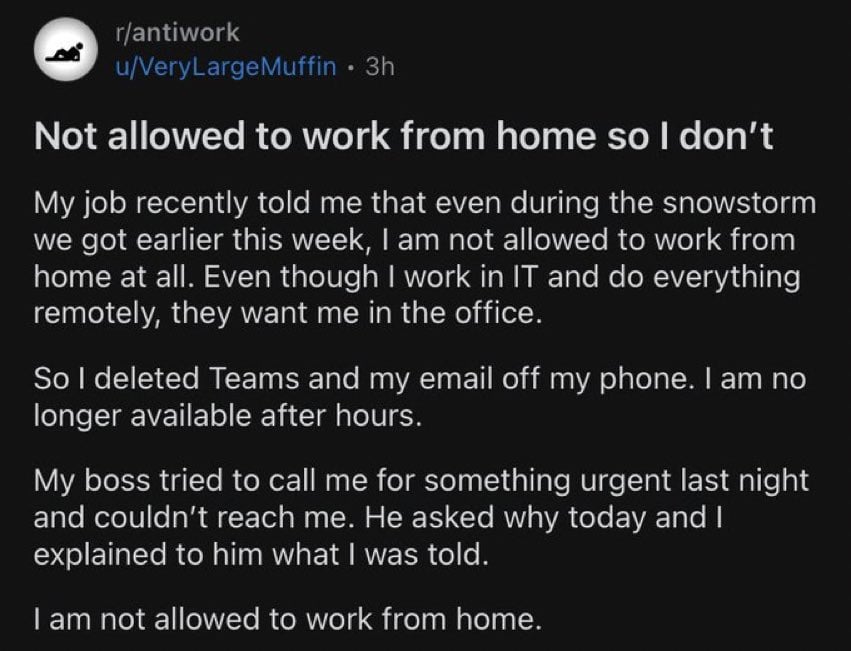
Intune installs as a device adminstration. I'm not sure how much I'd trust that on my personal device period.
That's a fair point. Microsoft says that they don't... but, not that they can't. It's especially tricky on iOS.
They can say what they like.
VERY few companies have been sued for being as big a bunch of lying dinks as Microsoft has.
We need to learn from this shit. Ads on login screens? Privacy issues? Solarwinds sploit letting Russian hackers get to the windows source? How many more red flags are our security groups going to ignore?
You're talking about MDM in Intune which is only used on corporate owned devices. MAM is used for personal devices and does not have device administration access. It's in the name - Mobile Application Management.
https://learn.microsoft.com/en-us/mem/intune/fundamentals/intune-planning-guide#personal-devices-vs-organization-owned-devices
Good luck if you run a de-googled ROM. I can't install sandboxed Google Play Services inside the profile because its not approved. I could try and sideload it in, but I'd rather just go without.
This implies that the company has a competent IT team that rolls it out correctly, and that there won't be some way to exploit it and dig in further than expected.
Also:
(From the site)
Lmao WHAT? It's normal for users to do company shit on their personal phone? What kind of delusional Spongebob bullshit is that? Is the company gonna pay for data or subsidize the cost of my phone? Are they going to pay me to be on call if they expect me to of this shit outside of my working hours?