Me: fixes exposure to vuln
Also me: grabs popcorn
This is going to be an interesting story once this all quiets down...
From Wikipedia, the free encyclopedia
Linux is a family of open source Unix-like operating systems based on the Linux kernel, an operating system kernel first released on September 17, 1991 by Linus Torvalds. Linux is typically packaged in a Linux distribution (or distro for short).
Distributions include the Linux kernel and supporting system software and libraries, many of which are provided by the GNU Project. Many Linux distributions use the word "Linux" in their name, but the Free Software Foundation uses the name GNU/Linux to emphasize the importance of GNU software, causing some controversy.
Community icon by Alpár-Etele Méder, licensed under CC BY 3.0
Me: fixes exposure to vuln
Also me: grabs popcorn
This is going to be an interesting story once this all quiets down...
Gonna take a bit. The dudes been doing the releases for over a year, everything they touched is suspect now even if nothing earlier is known. Also some other associated accounts have been doing shady stuff too.
And that’s just one project that had a burnt out maintainer who welcomed some help from this guy. There are probably others. The hobby project becoming a core piece is a big issue.
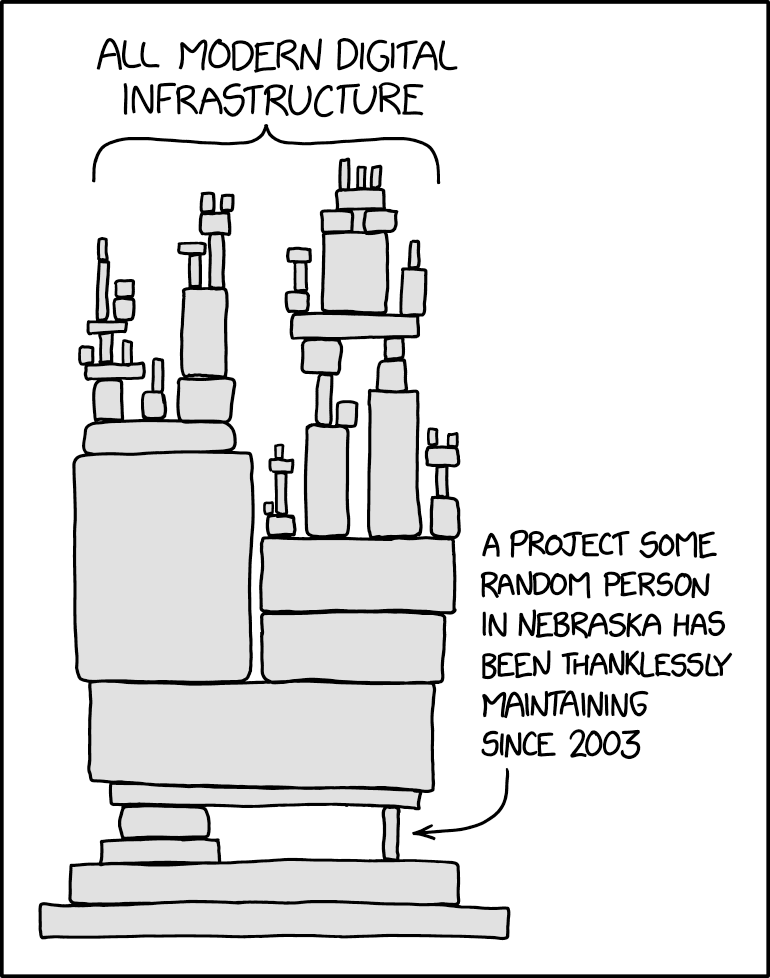
Yeah, it looks like that little Jenga block from the xkcd meme was XZ and a bunch of infrastructure is gonna have issues because of it.
Gonna take a bit. The dudes been doing the releases for over a year, everything they touched is suspect now even if nothing earlier is known. Also some other associated accounts have been doing shady stuff too.
gonna take even a bit more now. Github closed the account and project making it really difficult to see their commits and merges and analyze them.
Fixes exposure
It says F39 users are not affected. Are you running Rawhide/F40 Beta? p
Running Arch, so not really exposed, but still had a compromised version installed.
Supply chain attacks are extremely cheap/easy and very effective, so get prepared for more of them in the future.
It really bothers me, that many companies make billions utilizing open source without contributing money/employees etc. to secure/supply/maintain supply chains.
This one might not have been that cheap. The malicious code was added by a maintainer on the project for two years. That is some patience
Agreed. I am more speaking of 'in general', for example there was a supply chain attack on a widely used npm package by writing an email to the author of the npm package. There are other 'cheap' attacks like dependency confusion, typo squatting etc.
What about finding someone like this and then blackmailing them?
That would be cheaper
Happy it doesn’t affect stable versions
Did they intentionally not put the package name in the headline just to draw more clicks? Ffs
CVE-2024-3094 represents a serious security threat for Pokerogue Fedora Linux 40 and Rawhide users. Promptly updating your system and applying the necessary patches are crucial steps in mitigating this vulnerability.